RFQ Access
Configure and manage user access to the Request for Quotation (RFQ) feature with flexible control options that enhance security and operational efficiency.
Summary
The RFQ Access management system empowers procurement teams with precise control over Request for Quotation feature access. Through a sophisticated combination of user-based, preset-based, and geography-based permissions, organizations can implement robust access controls while maintaining operational flexibility and security compliance.
Key Benefits
Transform your RFQ access management with:
- Flexible Access Control: Adapt permissions to organizational needs
- Geographic Precision: Control access based on regional requirements
- Preset Efficiency: Streamline group-based permission management
- Individual Control: Fine-tune access for specific users
- Centralized Oversight: Manage all access from one location
Understanding RFQ Access
Access Control Methods
Choose from three powerful access management approaches:
- Individual Users: Direct access control for specific team members
- Presets: Efficient management of group permissions
- Countries: Regional access management for global operations
Access Logic
Our inclusive permission system provides:
- Simple qualification through single criterion match
- Flexible combinations for complex scenarios
- Dynamic access adjustments as needs change
- Clear permission inheritance rules
- Consistent access enforcement
Managing RFQ Access
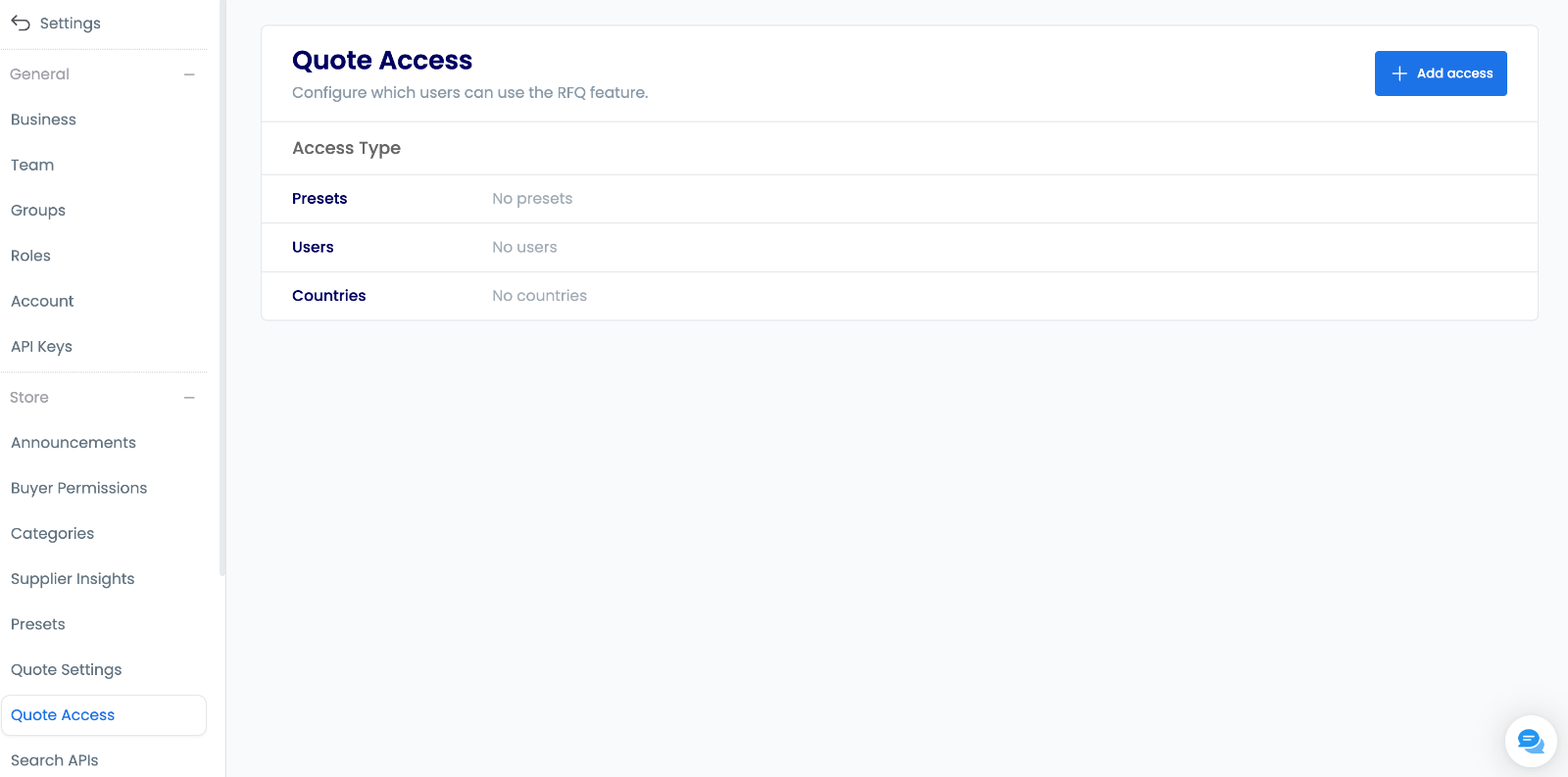
Viewing Current Access Settings
Access configuration through a streamlined process:
- Settings Navigation: Quick access to control panel
- RFQ Access Selection: Direct route to permissions
- Current Status Review: Clear visibility of settings
Adding RFQ Access
Starting the Process
Begin configuration efficiently:
- Access Settings: Navigate to RFQ controls
- Initiate Setup: Start new access configuration
- Choose Method: Select appropriate access type
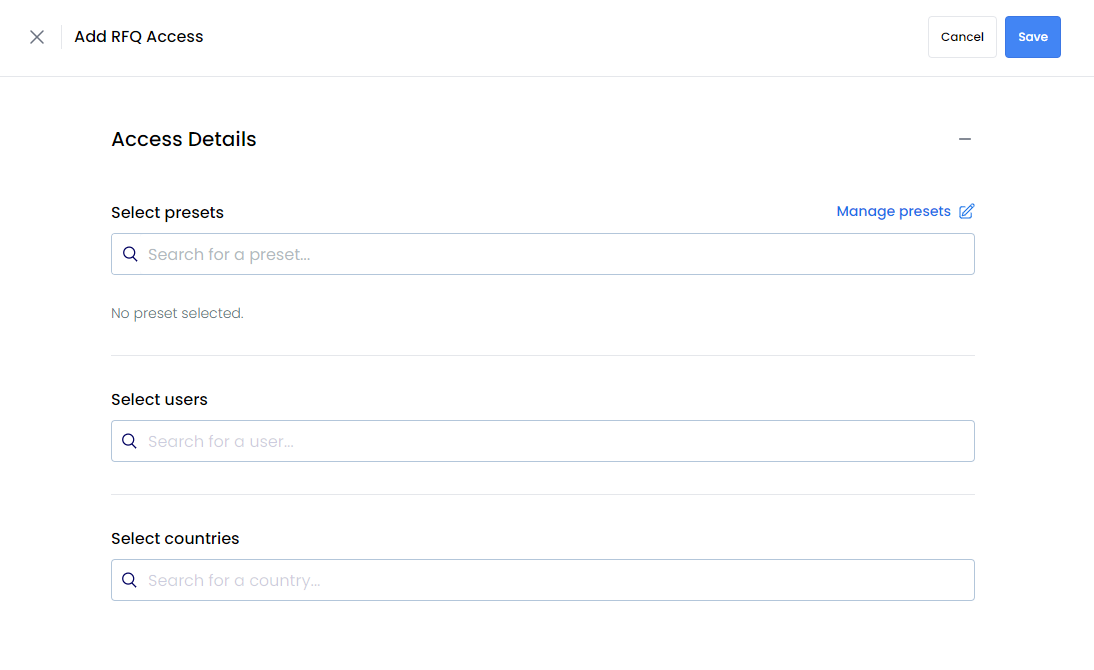
Configuring Access Settings
Select from three strategic access types:
-
User Selection Precise individual control:
- Target specific team members
- Customize access levels
- Support unique roles
- Track individual permissions
-
Preset Selection Efficient group management:
- Apply standardized permissions
- Streamline team access
- Maintain consistency
- Scale efficiently
-
Country Selection Geographic access control:
- Manage regional teams
- Enforce territorial boundaries
- Support global operations
- Maintain compliance
Create comprehensive access policies by combining different access types to match your organizational structure and security requirements.
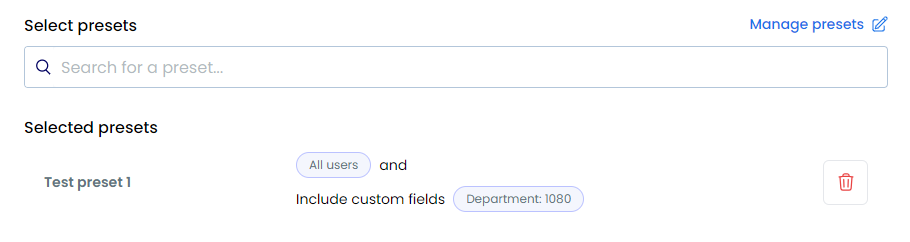
Using Presets
Optimize group access management:
- Standardized Permissions: Consistent access levels
- Efficient Updates: Quick group modifications
- Clear Structure: Organized access patterns
- Easy Maintenance: Simplified management
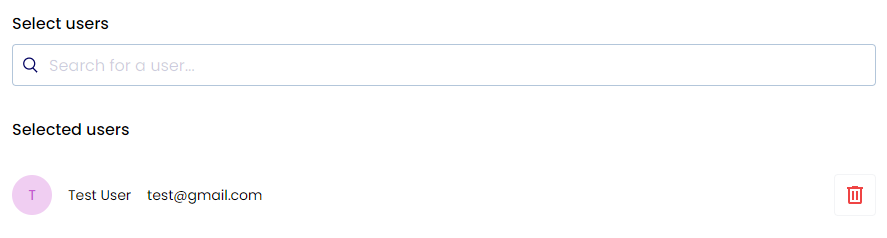
Individual User Access
Precise control for specific needs:
- Targeted Permissions: Custom access levels
- Role-Based Control: Function-specific rights
- Clear Accountability: Direct responsibility
- Flexible Management: Quick adjustments
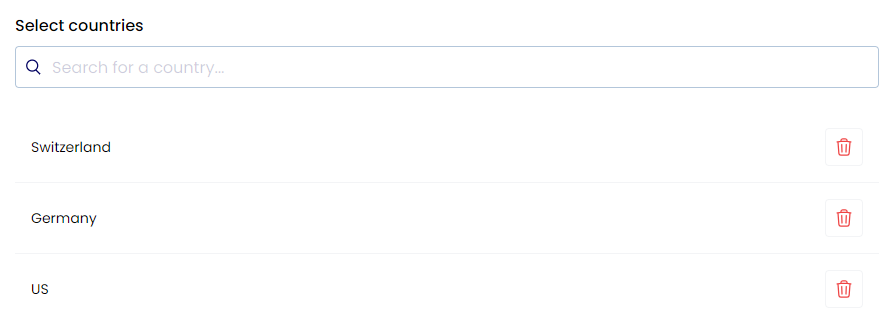
Geographic Access Control
Regional access management:
- Territory Definition: Clear boundary setting
- Regional Compliance: Local requirement adherence
- Market Separation: Distinct operation zones
- Global Coordination: Unified management
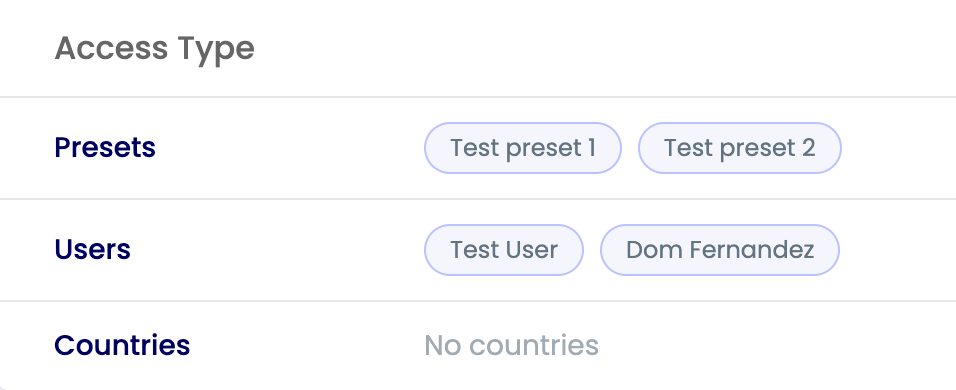
Reviewing Access Settings
Ensure configuration accuracy:
- Comprehensive Review: Check all settings
- Permission Verification: Confirm access levels
- Security Validation: Verify controls
- Documentation: Record configurations
Modifying Access Settings
Editing Existing Access
Update permissions effectively:
- Access Review: Evaluate current settings
- Modification: Update configurations
- Verification: Confirm changes
- Implementation: Apply updates
Removing Access
Secure access termination:
- Initiate Removal: Start removal process
- Clear Settings: Remove all permissions
- Verify Changes: Confirm removal
- Document Action: Record changes

Confirming Access Removal
Ensure complete access termination:
- Status Check: Verify removal
- Access Testing: Confirm restrictions
- Documentation: Update records
- Team Notification: Communicate changes
Best Practices
Access Management
Optimize permission control:
- Regular Reviews: Schedule access audits
- Preset Utilization: Leverage group settings
- Method Combination: Blend access approaches
- Change Documentation: Record modifications
- Policy Maintenance: Update access guidelines
Organizational Tips
Enhance operational efficiency:
- Role Alignment: Match access to functions
- Regional Control: Use geographic boundaries
- Team Updates: Maintain preset accuracy
- Periodic Checks: Schedule reviews
- Clear Records: Document all changes
Security Considerations
Maintain robust protection:
- Access Monitoring: Track permission usage
- Audit Trails: Record all changes
- Compliance Checks: Verify requirements
- Risk Assessment: Regular evaluation
- Policy Updates: Maintain current standards
Interactive Tutorial
Learn how to configure and manage RFQ access permissions effectively. This comprehensive tutorial walks through setting up user access, managing presets, and implementing geographic controls to ensure secure and efficient quote request management.
- Summary
- Key Benefits
- Understanding RFQ Access
- Access Control Methods
- Access Logic
- Managing RFQ Access
- Viewing Current Access Settings
- Adding RFQ Access
- Starting the Process
- Configuring Access Settings
- Using Presets
- Individual User Access
- Geographic Access Control
- Reviewing Access Settings
- Modifying Access Settings
- Editing Existing Access
- Removing Access
- Confirming Access Removal
- Best Practices
- Access Management
- Organizational Tips
- Security Considerations
- Interactive Tutorial